Cryptojacking cybercrime and Laws in India & USA
Cryptojacking (aka illegal cryptomining) is the practice of infecting a target with malware that uses a computer’s processing power to mine for cryptocurrencies without the owner’s consent or knowledge. Monero is one of the most common cryptocurrencies that is mined by hackers.
While the crypto-miner is running the user will notice a very high graphics card and/or CPU usage level. The browser could use 40% or more of your available computer power. This means that the computer or smartphone will run slower, the battery will drain faster and the temperature of the device might increase as long as the script is running. Moreover, an increased workload on the device results in a higher electricity bill.
How does cryptojacking works?
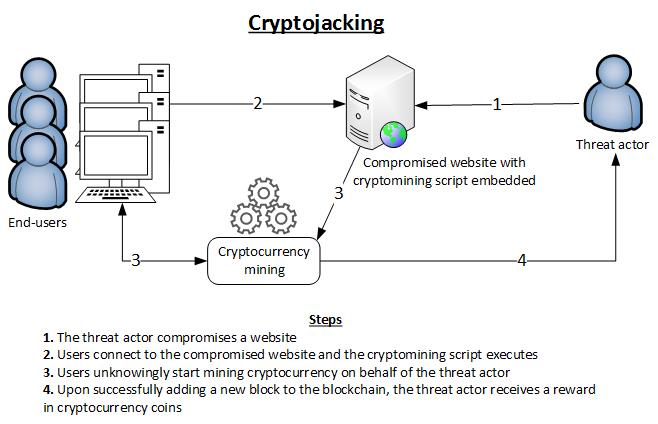
Cryptojacking works off a user's browser or can be plugged into popular websites, that will then use resources from a visitor's PC using their browser.
Hackers insert low-risk malware by targeting individual computers/Mobile phones or take the simpler and more popular route of embedding such malware on large online portals.
Using the latter makes more sense as such portals see massive traffic. These could range from unprotected government websites to news websites and even those belonging to companies providing services online, which see lots of traffic on a daily basis with plenty of users logged in to get things done. Modern manufacturing plants too can be a target with so many computers being online and always running at the same time.
So when a government portal is found to have malware running crypto mining operations, all of the users accessing the same can expect their systems to be infected as well.
Once the malware has been embedded on such websites, it reaches out to individual users accessing those websites for services and then hijacks their web browsers, slowing down their systems tremendously because of the mining process being conducted on each of their systems.
In the case smartphones, the effects are similar.
In the first instance of a major 'cryptojacking' attack in India, more than 2,000 computers of the Aditya Birla Group were reportedly hacked by miners to mine cryptocurrencies.
Companies are slowly taking note of the latest kind of cyber attack and working for solutions to prevent it. Google recently announced it would ban all extensions that involved cryptocurrency mining from its Chrome browser – regardless of whether the mining was done openly or in secret.
How to discover?
To see if the browser is currently mining crypto-currencies you can use the
task manager (windows) or the activity monitor (apple):
Windows task manager
1. Open the task manager by right clicking the task bar and selecting “task manager”
2. Click on “More details”
3. Go to the performance tab, to see your CPU usage
Macintosh activity monitor
1. Hit Command+Spacebar to bring up the Spotlight search field
2. Type in “Activity Monitor”
3. Hit the Return key when “Activity Monitor” populates in the spotlight results
4. You are now in Activity Monitor where you can manage and manipulate tasks
Case & Arrest in Japan
In July 2018, the first case of prosecution in Japan -- and potentially the world -- the 24-year-old Yoshida Shinkaru was sentenced to one year in prison, which has been suspended for three years. In this case, Coinhive was reportedly planted within an online gaming cheat tool which was then made available for download.
Law in India
A criminal case under S43(a) read with S(66) of The IT Act,2000 can be filedThe section says, If any person without permission of the owner or any other person who is in charge of a computer, computer system or computer network- accesses or secures access to such computer, computer system or computer network punishment of imprisonment up to three years, a fine of up to Rs. 5 Lakhs or Both.
Victims can claim damages and compensation under Section43(a) for a civil remedy.
Law in USA
The federal statute that creates both civil and criminal penalties for “computer hacking” is the Computer Fraud and Abuse Act (CFAA), 18 U.S.C. § 1030. Under the CFAA, it is punishable to “exceed authorized access” to a protected computer. The term, “protected computer” has been very broadly interpreted, and covers essentially all computers connected to the internet. While there has been some disagreement amongst the courts regarding the interpretation of “access” to a computer, the Department of Justice’s (DOJ) guidance suggests that cryptojacking would likely be an offense under the CFAA. Notably, the DOJ contends that under §§ 1030(a)(5) and 1030(c)(4)(A)(i)(VI) damage to a protected computer may result from the appropriation of the computer’s resources by malicious code—and the latter subsection covers “malware” of the type that might not cause enough damage in a single instance to trigger felony liability but affects more than 10 protected computers in a year.
What can be done about it?
1. User consent and opt-out option. After the extensive abuse of Coinhive, the company behind it, released a new version called “Authedmine”, which explicitly requires user consent before initiating cryptomining. Legitimate businesses that choose solutions similar to Coinhive should request user consent before running any cryptomining code in their browsers, while offering them the option to opt-out too.
2. Consider using an ad-blocker. Well known ad-blockers quickly added support for blocking Coinhive. Hence users that make use of ad-blockers should not worry about cryptomining JavaScript running in the background. Having said that, while ad-blockers can be beneficial against unwanted and often malicious advertisements and scripts, they can also be damaging for legitimate companies whose revenue relies on advertisements. Therefore, users may still use an ad-blocker but whitelist websites accordingly.
3. Consider using a browser extension for blocking cryptomining scripts. Developers have also created browser extensions that block Coinhive and other similar cryptomining scripts. Users can search for these extensions in their browsers’ market place.
4. Update your antivirus/anti-malware software. Antivirus and anti-malware solutions already block cryptomining software, hence users are advised to keep them updated at all times.
5. Disable unnecessary browser extensions. Users are advised to disable/remove browser extensions they no longer use as it is often the case that a legitimate extension becomes malicious after an update. Hence, it is recommended to reduce the attack surface whenever possible by keeping installed extensions to a minimum.
Conclusion
Cryptojacking quickly became a new tool in the hands of cyber criminals, which shows once more that cyber criminals are ready to find novel ways and grasp new opportunities to make profit in. Cryptojacking is a fine example of how new technologies present both beneficial uses and the potential for harmful use. And, in some ways, cryptojacking is unique because it is dependent on decentralizing and privacy-enhancing technologies behind cryptocurrencies and uncertainties in the legal/regulatory frameworks surrounding the internet. It is the intersection of hardware development, cryptography, decentralization, and the law that makes it hard to predict how cryptojacking will continue to evolve. However, given the current state of the art, it appears that cryptojacking will continue to be a cybersecurity threat for the foreseeable future.
Prashant Mali is a practicing Bombay High Court Lawyer, Author & International Speaker who specialises in Cyber Law, Data Protection Law & Privacy.
He can be reached on cyberlawconsulting@gmail.com
To be continued and updated going ahead



Thank you dear, I found your information really useful. I would like to say thanks once again for this information. Keep posting all the new information.
ReplyDeleteCyber Security
CyberCrime
Cybersecurity
I invite you to the page where you can read with interesting information on similar topics. cryptocurrency widgets
ReplyDelete