is a Malware(virus types) which is sent to your computer via email or via an attachment of a fake invoice then that malware(malicious software) encrypts your hard disk and whole data becomes meaningless like special characters ं$#़॥ like this only one jpg file u can open.
Then only in this jpg file there are instructions to pay ransome via bitcoin. Once u pay the hard disk is decrypted I.e made meaningful.
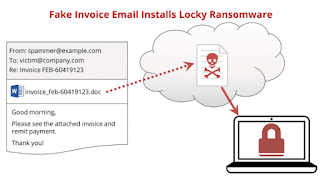
The victim receives an email that requests payment on an attached "invoice", usually a Word file. The attachment contains some sort of executable code, like a VBA macro, that downloads the actual malware from a web site and runs it, encrypting the data on the victim's local and networked hard drives. It then displays a screen that demands a ransom to decrypt the data.
The victim receives an email that requests payment on an attached "invoice", usually a Word file. The attachment contains some sort of executable code, like a VBA macro, that downloads the actual malware from a web site and runs it, encrypting the data on the victim's local and networked hard drives. It then displays a screen that demands a ransom to decrypt the data.
WHAT TO DO WITH LOCKY?
Backup regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands. Don’t enable macros in document attachments received via email. Microsoft deliberately turned off auto-execution of macros by default many years ago as a security measure. A lot of malware infections rely on persuading you to turn macros back on, so don’t do it!Be cautious about unsolicited attachments. The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out. Don’t give yourself more login power than you need. Most importantly, don’t stay logged in as an administrator any longer than is strictly necessary, and avoid browsing, opening documents or other “regular work” activities while you have administrator rights.Consider installing the Microsoft Office viewers. These viewer applications let you see what documents look like without opening them in Word or Excel itself. In particular, the viewer software doesn’t support macros at all, so you can’t enable macros by mistake!Patch early, patch often. Malware that doesn’t come in via document macros often relies on security bugs in popular applications, including Office, your browser, Flash and more. The sooner you patch, the fewer open holes remain for the crooks to exploit.
..Advocate Prashant Mali
Cyber Security & Law Expert


No comments:
Post a Comment
Note: Only a member of this blog may post a comment.